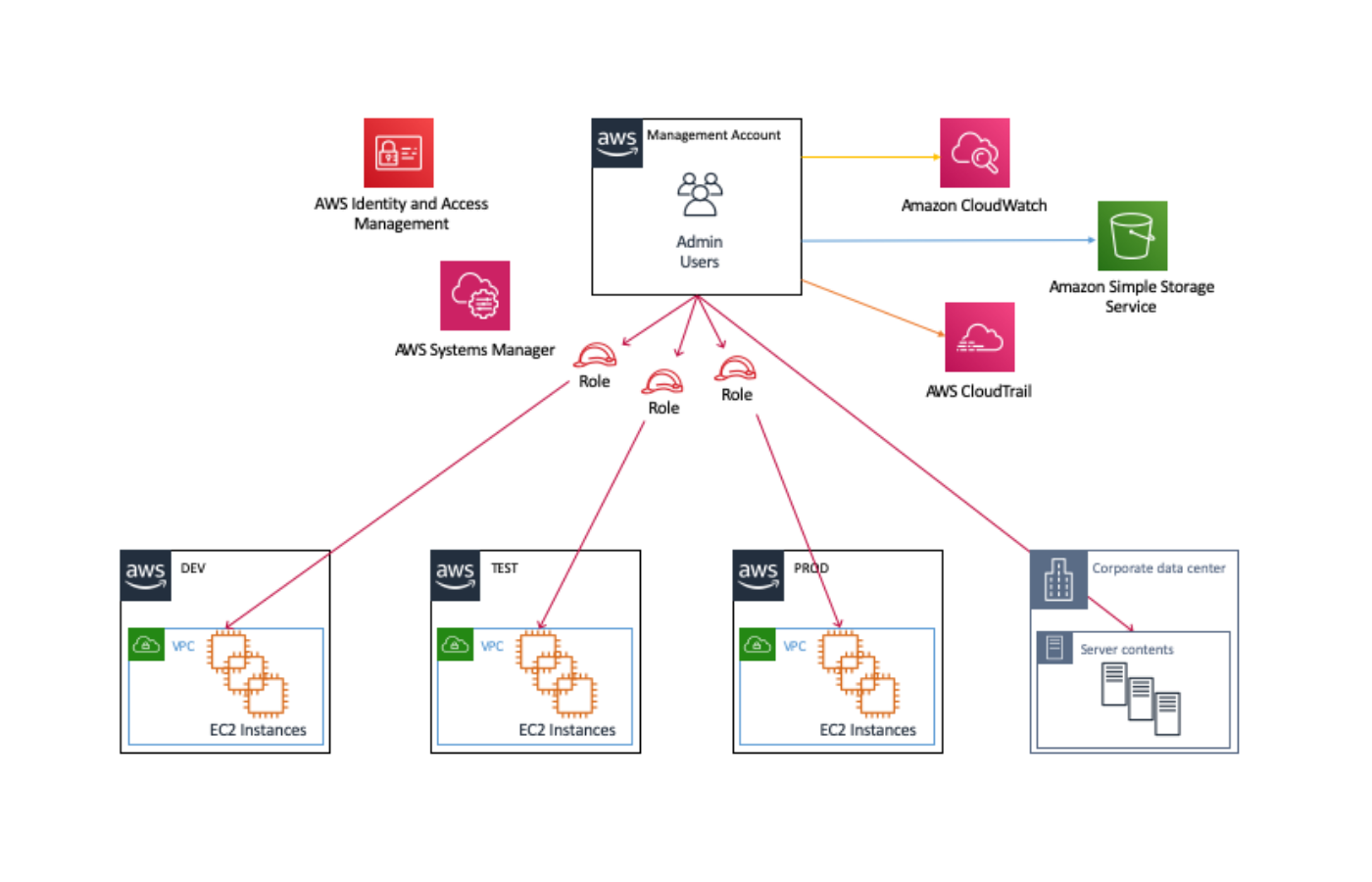
The key sharing can be avoided and access to the instance can be limited using AWS IAM permissions Read our blog on the issues associated with sharing SSH keys here It provides an easy access Access an Amazon EC2 instance using Session Manager port forwarding Note Before attempting to start a session, ensure that you have completed the steps above to setup Session ManagerFor more information, see getting started with Session Manager To use the AWS Systems Manager command line interface (AWS CLI) for port forwarding, the Session Manager Martha and Richard now have full access to Amazon EC2 and Amazon S3 in the developer accounts and readonly access in the production accounts Users sign into the User Portal to access accounts Martha and Richard receive email
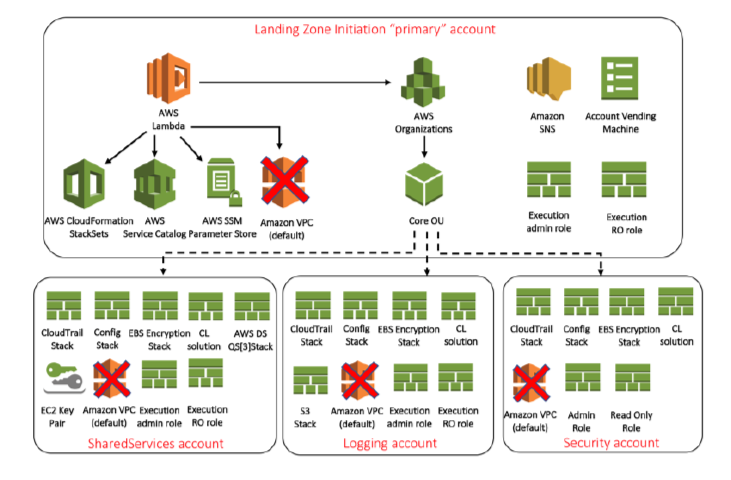
Aws Landing Zone Creating A Corporate Structure In Aws Lcloud
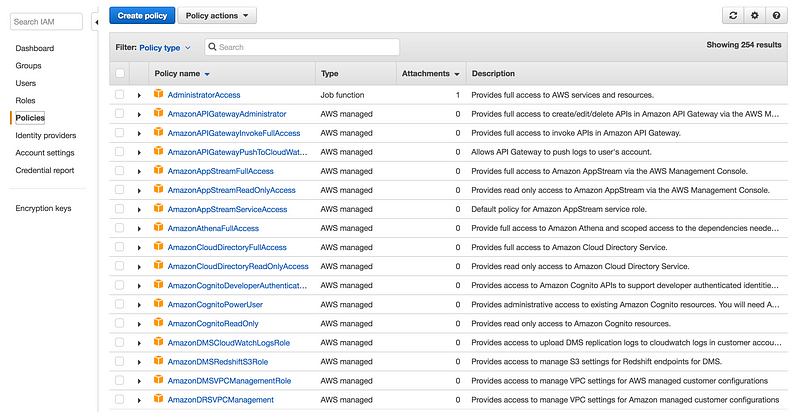
Amazonssmreadonlyaccess
Amazonssmreadonlyaccess-Amazon EC2 Simple Systems Manager (SSM) is an Amazon Web Services (AWS) logs, you need to launch the instance with a role that has access to CloudWatch and SSM Amazon Web Services – EC2 Simple Systems Manager November 15 Page 10 of 22 For an example IAM role, which combines SSM and CloudWatch with the Or if you are new, you can access at my Github We then need to install couple of CDK dependencies for AWS CodePipeline, AWS CodeBuild, and Amazon ECR Execute the following command npm update npm install @awscdk/awscodepipeline @awscdk/awscodepipelineactions @awscdk/awscodebuild @awscdk/awsecr @awscdk/awsssm @awscdk/aws




Compliance Check Of Sap Systems Using Aws Config Part I Sap Blogs
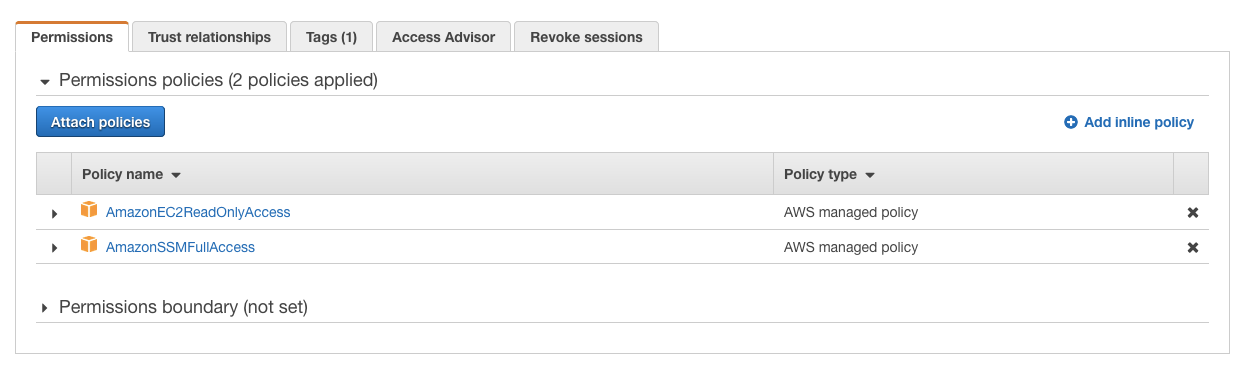
Helpful 1 for ecsexecchecker tool mentioned by Mats, it would be helpful for most cases Looking at the logs we have in ECS & Fargate, the backend and agent are looking good The issue instead is that the ExecuteCommand agent is not able to start up inside the containers and this usually happens for the following scenarios (please note ECS The minimumneeded permission is actually only read access on a few system managerspecific s3 buckets This is far more restrictive than the default recommended role shown in the getting started guide Anyone looking to follow the principle of least privilege will want to create a custom role with the minimal permission version given by Amazon Select Amazon EC2 Read Only Access during Permissions step Step 3 Set EC2ReadOnly User Create a specific EC2readOnlyUser during Users step Step 4 Generate Group, Policy, User and Credentials Review and confirm the creation of the Group and User, and the generation of the EC2 Credentials for this user
Option 1 Open the IAM console at https//consoleawsamazoncom/iam/ In the navigation pane, choose Policies , and then update the permissions policy for the user or role you want to allow to start SSH connections through Session ManagerCreates a new SSM String parameter with the values provided;If you would like to purchase boththe physical text and MyLab & Mastering, search for / * A Survey of Mathematics with Applications plus MyMathLab Student Access Card Access Code Card Package Package consists of / * A Survey of Mathematics with Applications /
Date First Available Manufacturer Citrix ASIN B006FAYZ4Q Best Sellers Rank #36,925 Free in Apps & Games ( See Top 100 in Apps & Games ) #1,373 in Productivity Customer Reviews 38 out of 5 stars 247 ratings After couple of minutes login to the AWS Systems Manager and, access the Session Manager Instance will be listed and, select the instance and start the Session It will open up an another tab with a connection to the instance, you can now run the commands directly from the console This session will be loaded with the " ssmuser " which isMake sure this fits by entering your model number Your personal cloud storage with 4TB large capacity doesn't have own WIFI:This NAS builtin 35inch 4TB storage, as long as it is powered and connected to the internet, you will be able to remote access and manage the storage data freely at anywhere by PC/Mobile phone,without geographical restrictionsPoint to Point(P2P)




Aws Identity And Access Management Iam Noise




Discovering Amazon Web Services Documentation For Bmc Discovery Content Reference Bmc Documentation
For example, if all the images are stored in a specific prefix within the bucket, it would be better to grant read permission to the prefix and not the full bucket To limit other permissions such as write access, ensure that your bucket access control list (ACL) does not permit public write access Next, for S3 Block Public Access you couldThe Session document schemaVersion must be 10, and the sessionType of the document must be InteractiveCommands You can then create AWS Identity and Access Management (IAM) policies that allow users to access only the Session documents you define This custom permission set will allow you to get the visibility you need, while still enforcing the principle of least privilege You will have access to the readonly information you need, without asking your administrator to provide the attestation AWS Control Tower sets up AWS Single SignOn (AWS SSO) with a native default directory AWS Control Tower comes with a set




Amazon Ec2 Systems Manager User Guide Pdf Free Download
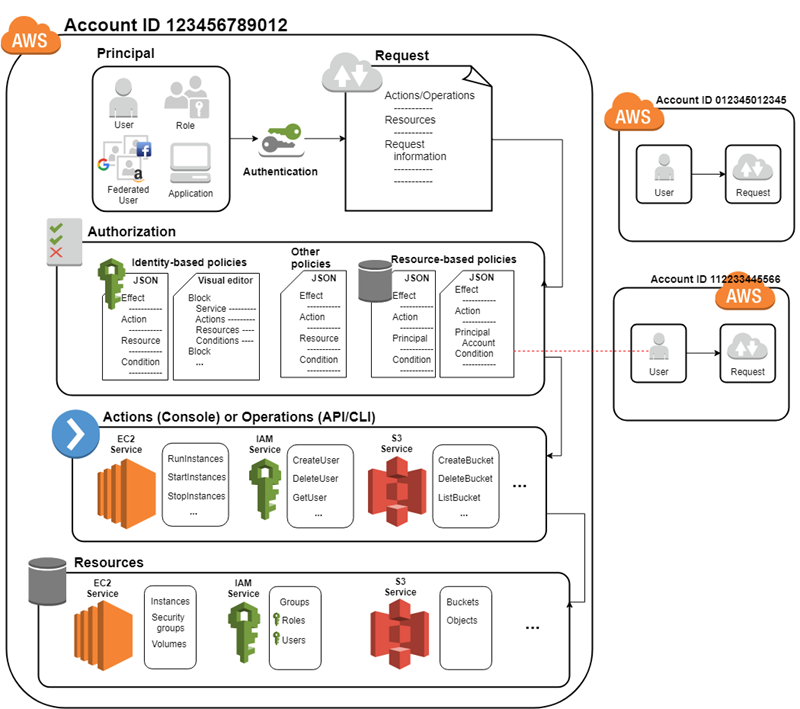



Understanding How Iam Works Aws Identity And Access Management
The reason you received "AccessDeniedException" is that the IAM role you attached to this instance doesn't contain correct policy In order to use AWS System Manager service, your instance need to have permission for System Manager API operation Please verify your instance is configured correctly and find more detailed information from eshmu commented on I found one easy workaround by using an AWSprovided SSM document aws ssm startsession target documentname AWSStartInteractiveCommand parameters command="bash l" This will put you into a bash shell when the SSM session is started SSM agent should be installed To install the SSM agent visit the AWS documentation here For some instances like Amazon Linux, Ubuntu Server 16,18 etc SSM agent is available by default IAM Role with EC2 readonly and SSM full access should be attached to the instance To create roles visit the AWS documentation here



Documentation Commvault Com Commvault V11 Others Pdf Commvault Amazon Sts Assumerole Activation Guide Pdf




Externalizing Configurations To Aws Ssm Parameter Store And Using In Asp Net Core Api Referbruv Codeblog
Access control configuration prevents your request from being allowed at this time Please contact your service provider if you feel this is incorrect Your cache administrator is webmaster Generated Fri, 5316 GMT by pocLinuxTC (squid/338) At C\ProgramData\Amazon\SSM\InstanceData\i08d3fcfa25c2b6233\document\orchestr ation To access the Systems Manager console, you must have a minimum set of permissions These permissions must allow you to list and view details about the Systems Manager resources and other resources in your AWS account Amazon WorkSpaces is a fully managed virtual desktop environment that runs on AWS It provides users with desktop cloudbased Microsoft Windows and Linux solutions that can be customized and configured to run seamlessly with your organization In this blog post, I show you how to install software onto a running WorkSpace using AWS Systems Manager,



Getting Started With Marklogic Server On Aws Marklogic Server On Amazon Web Services Aws Guide Marklogic 10 Product Documentation




Amazon Rds Read Replicas Cloud Relational Database Amazon Web Services
This item Standard Horizon SSM70H 25" Wired Remote Access Microphone (RAM4) STANDARD HORIZON GX1800GB Black 25W VHF/GPS/Second Station Explorer Series STANDARD HORIZON GX1850B Black 25W VHF/NME000/Second Explorer Series Standard STDMMB84 Flush Mount Kit for Most Standard Fixed Mount VHF Radios Setting up ReadOnly Access to S3 using AWS Identity and Access Management (IAM) A common problem with a very simple solution Let's say that you have an IAM user that you've created, and you want to provide that user readonly access to an S3 bucket With console access, users who interact with Amazon S3 to download and upload files can use a webbased GUI instead of constructing API calls Let's walk through two different policies one that grants programmatic access and another that grants console access Policy for Programmatic Access




Mastering Identity At Every Layer Of The Cake Sec401 R1 Aws Re In



Using Aws Systems Manager Ssh Free Access To Ec2 Instances Cloud Journey Io
Buy Invasion Zombie Read Apps & Games Reviews Amazoncom I am trying to determine the absolute minimum permissions required by the Amazon SSM agent in order to perform it's tasks, and would appreciate some assistance if there is a resource for this if anyone has a list (NOT the permissions from AmazonEC2RoleForSSM Amazon managed policy, as that grants (in my opinion) more permissions that appear to be necessary for SSM Is there an option to grant readonly access to an Amazon Web Services (AWS) account?




Aws Systems Manager Ug Amazon Web Services Cloud Computing



Aws Systems Manager Session Manager Bye Bye Bastion Hosts Pipetail Blog
When using IAM policies to restrict access to Systems Manager parameters, we recommend that you create and use restrictive IAM policies For example, the following policy allows a user to call the DescribeParameters and GetParameters API operations for a limited set of resources This means that the user can get information about and use all parameters that begin with proAWS_NODEJS_CONNECTION_REUSE_ENABLED (for Node 10x and higher functions) Amazon AWS Systems Manager Parameter Store String Enable readonly access for the associated AWS Lambda Function; The CloudWatchActionsEC2Access policy grants readonly access to CloudWatch alarms and metrics in addition to Amazon EC2 metadata It also grants access to the Stop, Terminate, and Reboot API actions for EC2 instances




Aws Automation Pack Accentedge We Offer Aws Products



Configuring Aws Monitoring
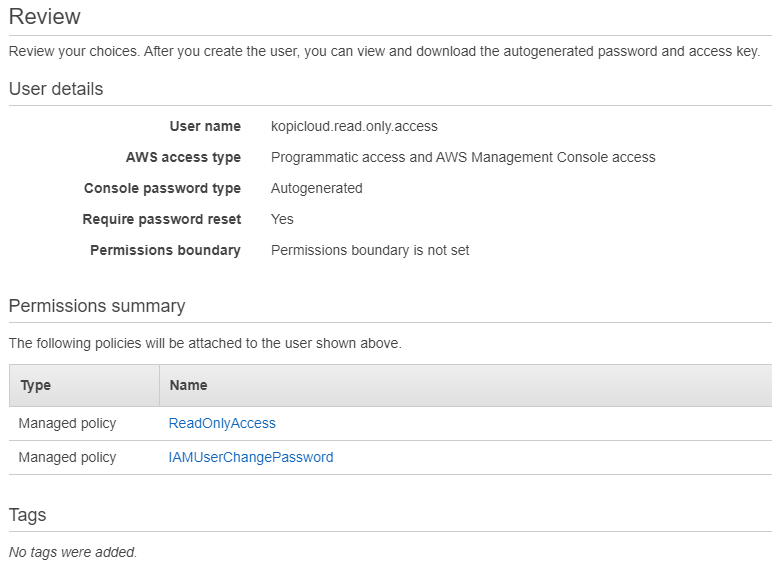
Restart SSM Agent Now you should see instance under System Manager Managed Instances Setting up the endpoint for SSM in the agent config file is not actually required The DNS table should have an entry that route traffic going to SSM endpoint to the private SSM GUIDE How to Create ReadOnly Access on AWS From the main console screen, type in IAM And select the suggested link From the IAM dashboard select the Users section and then Add user button Enter the new username for your readonly user (ABT_ReadOnly in this example), select the Programmatic access and AWS Management Console Access Instructions 1 From a local machine (for example, your laptop), run the SSH command to connect to instance1, using Session Managerbased SSH This command establishes a tunnel to port 3306 on instance2, and presents it in your local machine on port 9090



How To Grant Read Only Access On Amazon Web Services Aws By Guillermo Musumeci Medium




Red Team Vs Blue Team On Aws Dvc304 Aws Re Invent 18
Create the IAM role that has readonly access to Amazon RDS DB instances Attach the IAM policies to your IAM role according to your security requirements The aws iam createrole command creates the IAM role and defines the trust relationship according to theChoose items to buy together This item Standard Horizon SSM71H 25" Wireless Remote Access Microphone $ Only 1 left in stock order soon Ships from and sold by Amazoncom FREE Shipping Standard Horizon SCU30 Wireless Base Station Unit $ Only 2 left in stock Apr 4th, 18 447 pm Today we will use Amazon Web Services SSM Service to store secrets in their Parameter Store which we will encyrpt using KMS Then we will read the data from SSM and decrypt using our KMS key We will then end it off by writing a Python Script that reads the AWS credentials, authenticates with SSM and then read the secret



Github Managedkube Aws Ssm Interactive Sessions A Simple And Secure Way To Ssh Into Your Aws Ec2 Instances



Session Manager Feature Request Allow Read Only User Issue 146 Aws Amazon Ssm Agent Github
What I'd like to achieve is to be able to see instances and configurations without having to log in as a user who has administrative permissions to avoid accidental changes amazonwebservices amazon readonly accountAWS Systems Manager (formerly known as SSM) is an AWS service that you can use to view and control your infrastructure on AWS Using the Systems Manager console, you can view operational data from multiple AWS services and automate operational tasks across your AWS resources Systems Manager helps you maintain security and compliance by scanning your managed You must grant access by using an AWS Identity and Access Management (IAM) instance profile An instance profile is a container that passes IAM role information to an Amazon Elastic Compute Cloud (Amazon EC2) instance at launch You need to add SSM permission to your Instance Profile SSM Agent Ensure the latest SSM Agent on Target Instance




Amazon Quicksight Business Intelligence Service Amazon Web Services




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog
Access to the bastion host is ideally restricted to mazonssmregions3amazonawsThe first example uses Systems Manager Session Manager to drop the user directly into a command shell on the instance This can be done either from the AWS CLI Or the AWS Console This connectivity is purely through the SSM service Access is controlled via IAM and there are no Security Group rulesRSS AWS Systems Manager Agent (SSM Agent) is Amazon software that can be installed and configured on an EC2 instance, an onpremises server, or a virtual machine (VM) SSM Agent makes it possible for Systems Manager to update, manage, and configure these resources The agent processes requests from the Systems Manager service in the AWS Cloud, and then runs



Aws Identity And Access Management Iam Roles Sts Assume Role Via Aws Cli2 21




Building Secure Immutable Infrastructure On Aws Helecloud
Provide readonly access in an AWS environment is useful when a consultant, partner or contractor needs to examine your cloud environment WITHOUT being able to change anything AWS Identity andExample Readonly access To allow users to view all resources in the Amazon EC2 console, you can use the same policy as the following example Example Readonly access Users cannot perform any actions on those resources or create new resources, unless another statement grants them permission to do soFind helpful customer reviews and review ratings for Standard Horizon SSM71H 25" Wireless Remote Access Microphone at Amazoncom Read honest and




Aws Systems Manager Noise




Automated Configuration Of Session Manager Without An Internet Gateway Aws Management Governance Blog
This is an IAM resource policy, similar to bucket policies for Amazon Simple Storage Service (S3), and can be used, for example, to disable root access, enforce readonly access, or enforce intransit encryption for all clients Identitybased policies, such as those used by IAM users, groups, or roles, can override these default permissions Amazonssmagent unrecognized service (just installed it via docker) I have been struggling to figure out why I cannot start and stop the amazonssmagent service manually in a Kali Linux docker image running on an Ubuntu 041 LTS host Per their instructions, I have obtained the deb file and installed it with dpkg i Anyone who has access to session manager on a specific instance currently has sudo access (as the ssm user on the ec2 instance is part of the sudoers group) We have a use case where we would like to give users access to session manager to ssh onto an instance, but they shouldn't have sudo access (ie, read only access)




Compliance Check Of Sap Systems Using Aws Config Part I Sap Blogs




How To Automate Scap Testing With Aws Systems Manager And Security Hub Aws Security Blog




Amazon Ec2 Systems Manager User Guide Manualzz




Accessing An Amazon Rds Instance Remotely Using Aws Client Vpn Aws Database Blog




Session Manager Feature Request Allow Read Only User Issue 146 Aws Amazon Ssm Agent Github




Amazon Web Service Aws Jenkins Configuration Provar



Session Manager Feature Request Allow Read Only User Issue 146 Aws Amazon Ssm Agent Github



Page 3 100 Days Of Devops



Using The Aws Parameter Store In Net Core Mircea Oprea
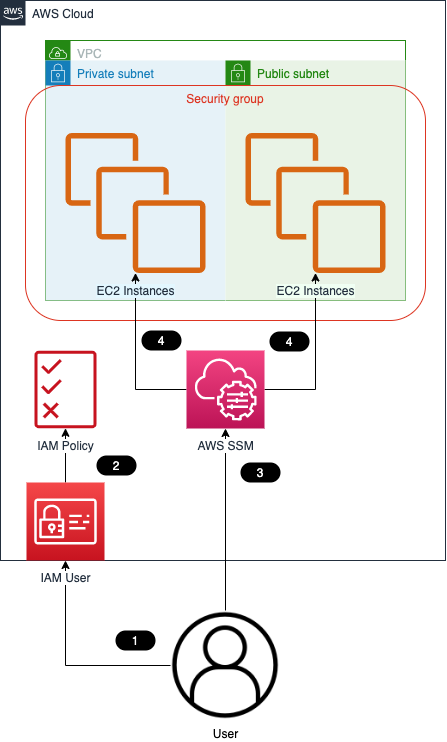



How To Access Ec2 Instance Via Ssh Without Exposing The Ssh Aws Tips And Tricks




Ssm Agent Creating Folders With Wrong Permissions Issue 286 Aws Amazon Ssm Agent Github




Compliance Check Of Sap Systems Using Aws Config Part I Sap Blogs




Configuring Aws Systems Manager Session Manager Run As Support For Federated Users Using Session s Aws Management Governance Blog



Docs Aws Amazon Com Systems Manager Latest Userguide Systems Manager Ug Pdf




Aws Programmatic Ponderings Page 3
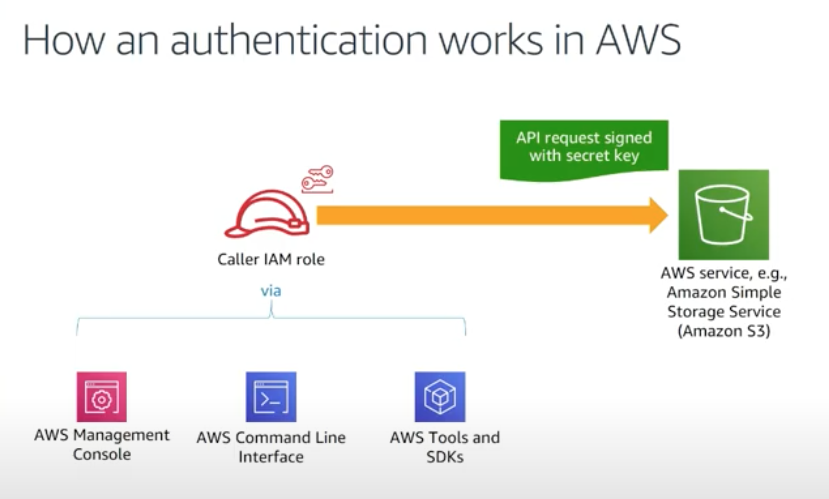



Aws Identity And Access Management Iam Policies Sts Assumerole And Delegate Access Across Aws Accounts 21




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog
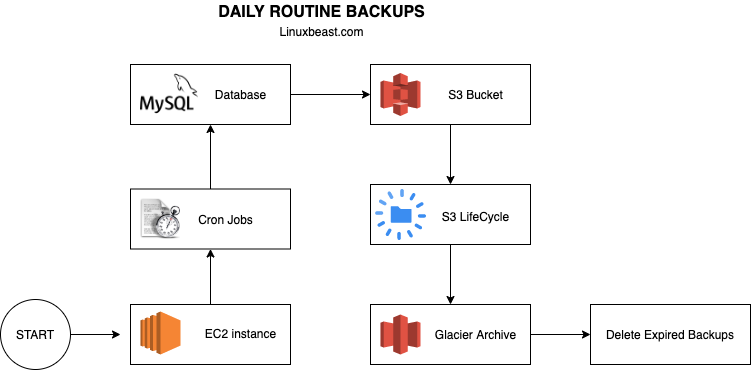



Automate Mysqldump Backup In Ec2 To Amazon S3 Linuxbeast




Spring Cloud Aws



Using The Aws Parameter Store In Net Core Mircea Oprea



Getting Started With Marklogic Server On Aws Marklogic Server On Amazon Web Services Aws Guide Marklogic 10 Product Documentation




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog
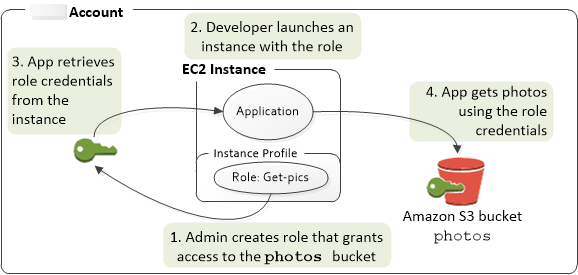



Using An Iam Role To Grant Permissions To Applications Running On Amazon Ec2 Instances Amazon Identity And Access Management




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog



Configure Container Security For Eks Mcafee Mvision Cloud



A Playbook To Secure Your Amazon Aws Infrastructure Using Centrify And Active Directory Part 3



1




Introducing Fine Grained Iam Roles For Service Accounts Aws Open Source Blog
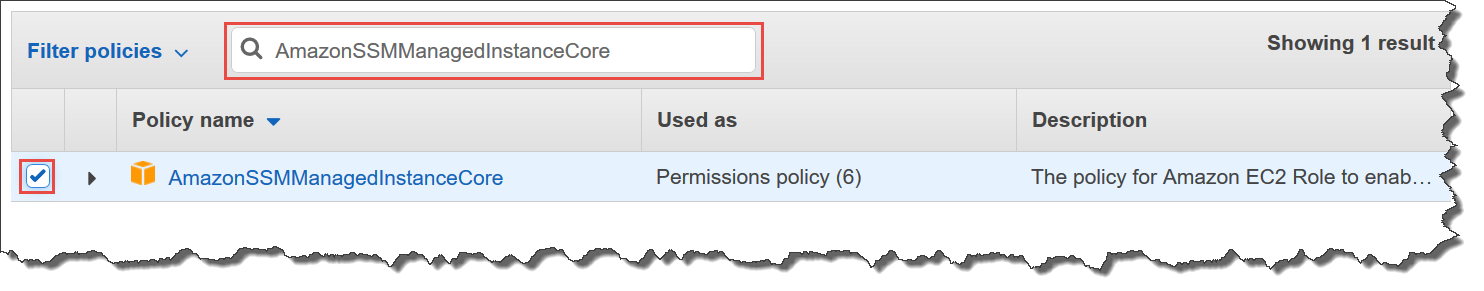



Step 4 Create An Iam Instance Profile For Systems Manager Aws Systems Manager




The Right Way To Store Secrets Using Parameter Store Aws Management Governance Blog
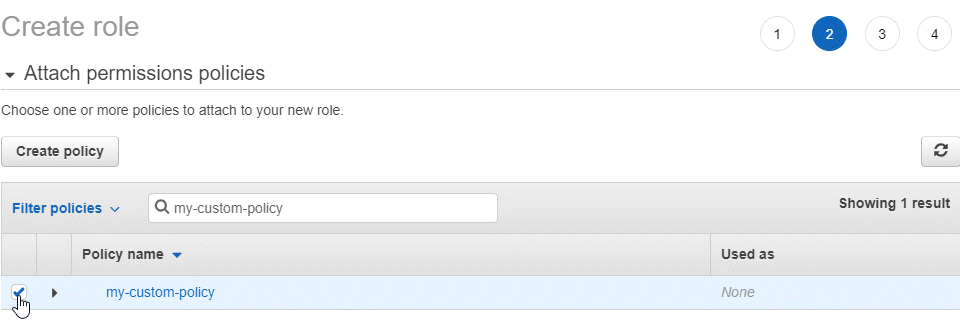



Getting Started With Marklogic Server On Aws Marklogic Server On Amazon Web Services Aws Guide Marklogic 10 Product Documentation




Software Deployment To Amazon Workspaces Using Aws Systems Manager Aws Management Governance Blog



Session Manager Feature Request Allow Read Only User Issue 146 Aws Amazon Ssm Agent Github




Compliance Check Of Sap Systems Using Aws Config Part I Sap Blogs



Q Tbn And9gctusdgyoyjmp5bksqwp3udd7sjoyk8 I7khr0oqntg Usqp Cau



1
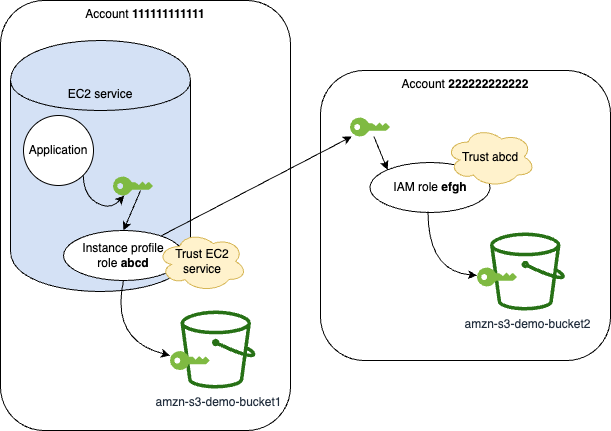



Using An Iam Role To Grant Permissions To Applications Running On Amazon Ec2 Instances Amazon Identity And Access Management




Aws Automation Pack Accentedge We Offer Aws Products




Compliance Check Of Sap Systems Using Aws Config Part I Sap Blogs



Getting Started With Marklogic Server On Aws Marklogic Server On Amazon Web Services Aws Guide Marklogic 10 Product Documentation




Aws Landing Zone Creating A Corporate Structure In Aws Lcloud




100 Read Information From Ssm Parameter Store Nodejs Aws Alien Attack Workshop
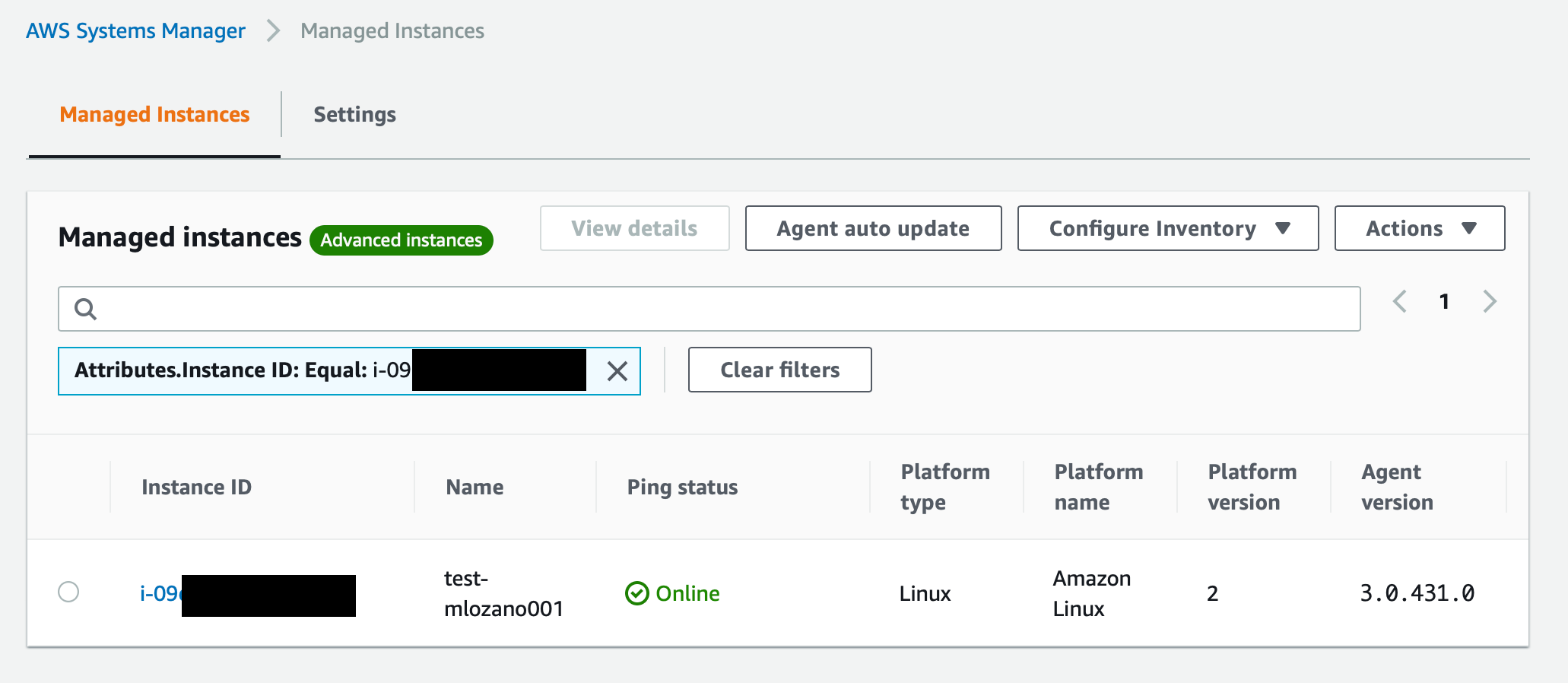



How To Access Ec2 Instance Via Ssh Without Exposing The Ssh Aws Tips And Tricks
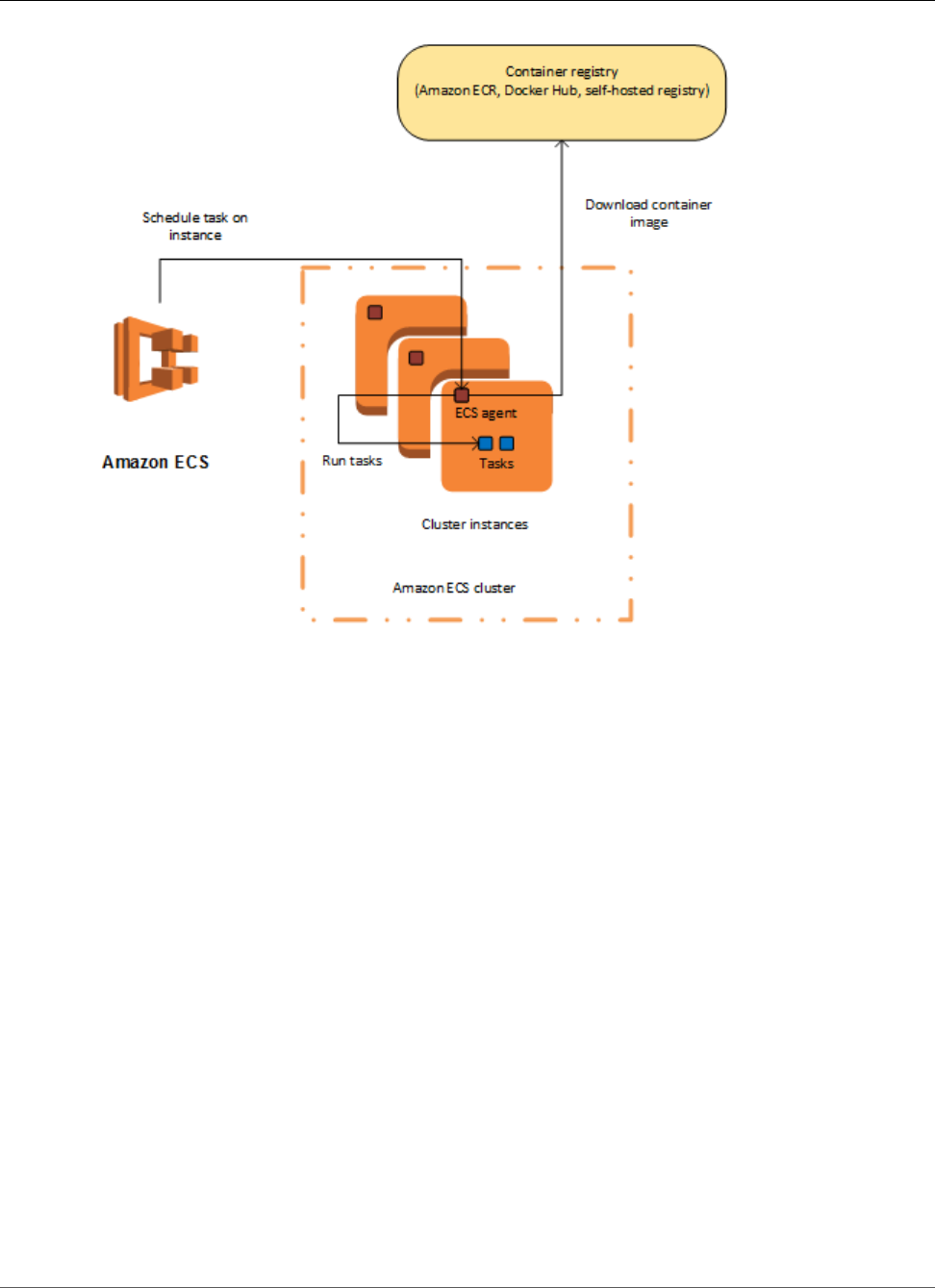



Amazon Ec2 Container Service Developer Guide Aws
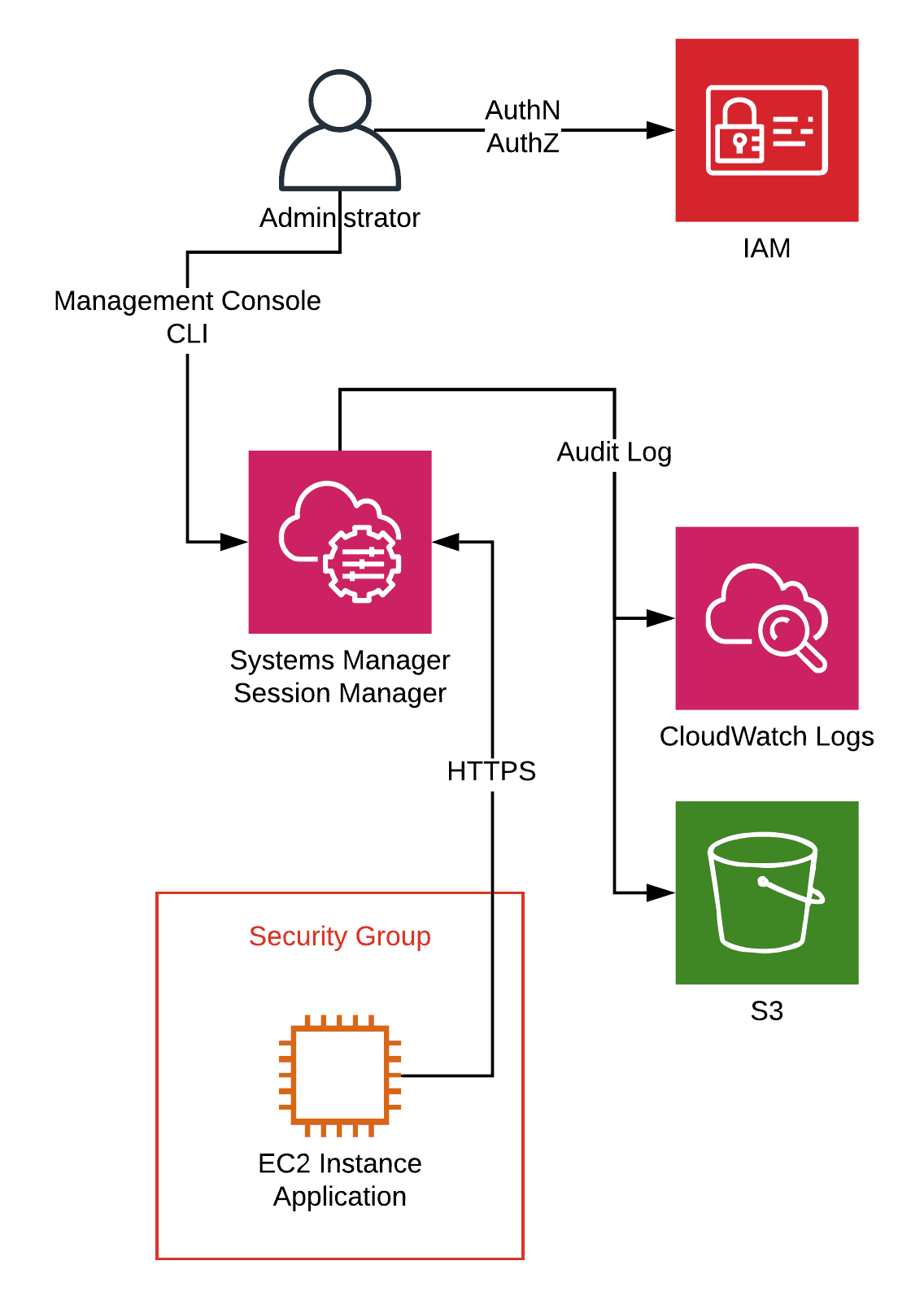



Goodbye Ssh Use Aws Session Manager Instead Cloudonaut



Amazon Ec2




Discovering Amazon Web Services Documentation For Bmc Discovery Content Reference Bmc Documentation




Terraform Aws Modules Iam Aws Terraform Registry




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog



1



How To Configure The Unified Cloudwatch Agent For Collecting Logs And Custom Metrics By Sandeep Harikumar Tensult Blogs Medium
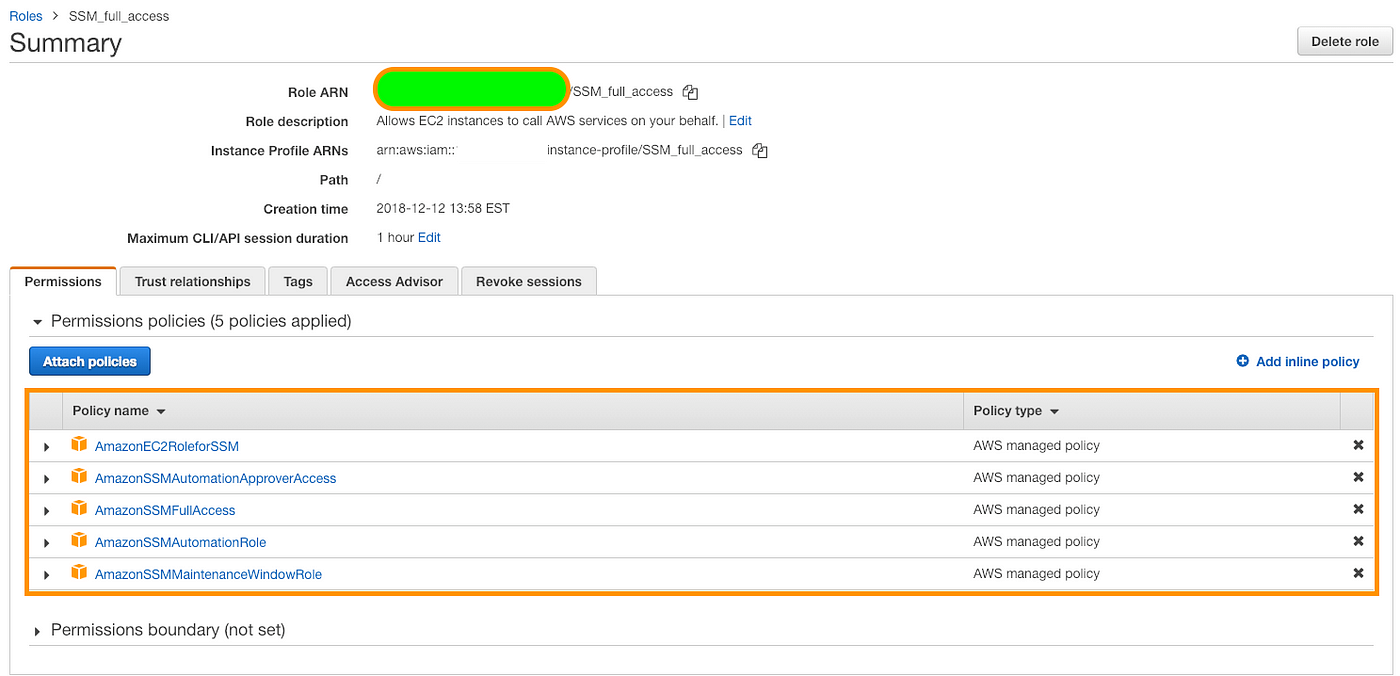



Using Aws Systems Manager Ssh Free Access To Ec2 Instances By Prabhu Barathi Medium




How To Enable Cross Account Access To The Aws Management Console Aws Security Blog




Join A Microsoft Active Directory Domain With Parameter Store And Amazon Ec2 Systems Manager Documents Aws Management Governance Blog
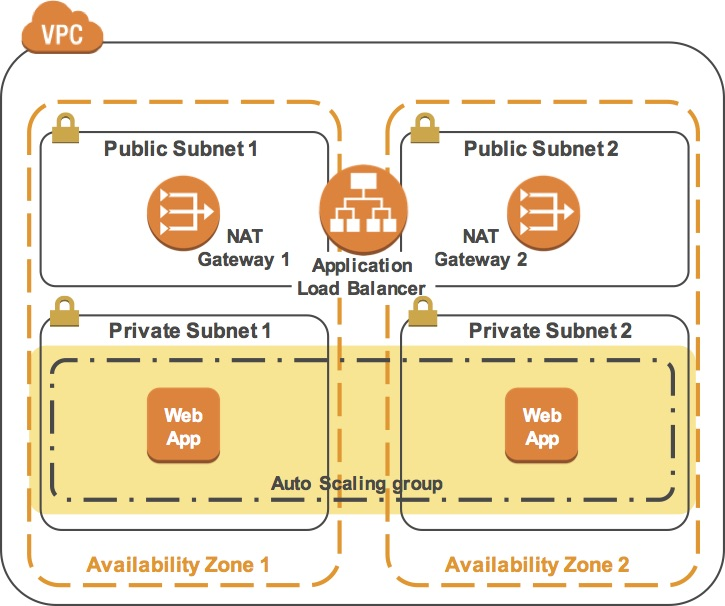



Aws Cloud Architecting Zacks Blog




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog
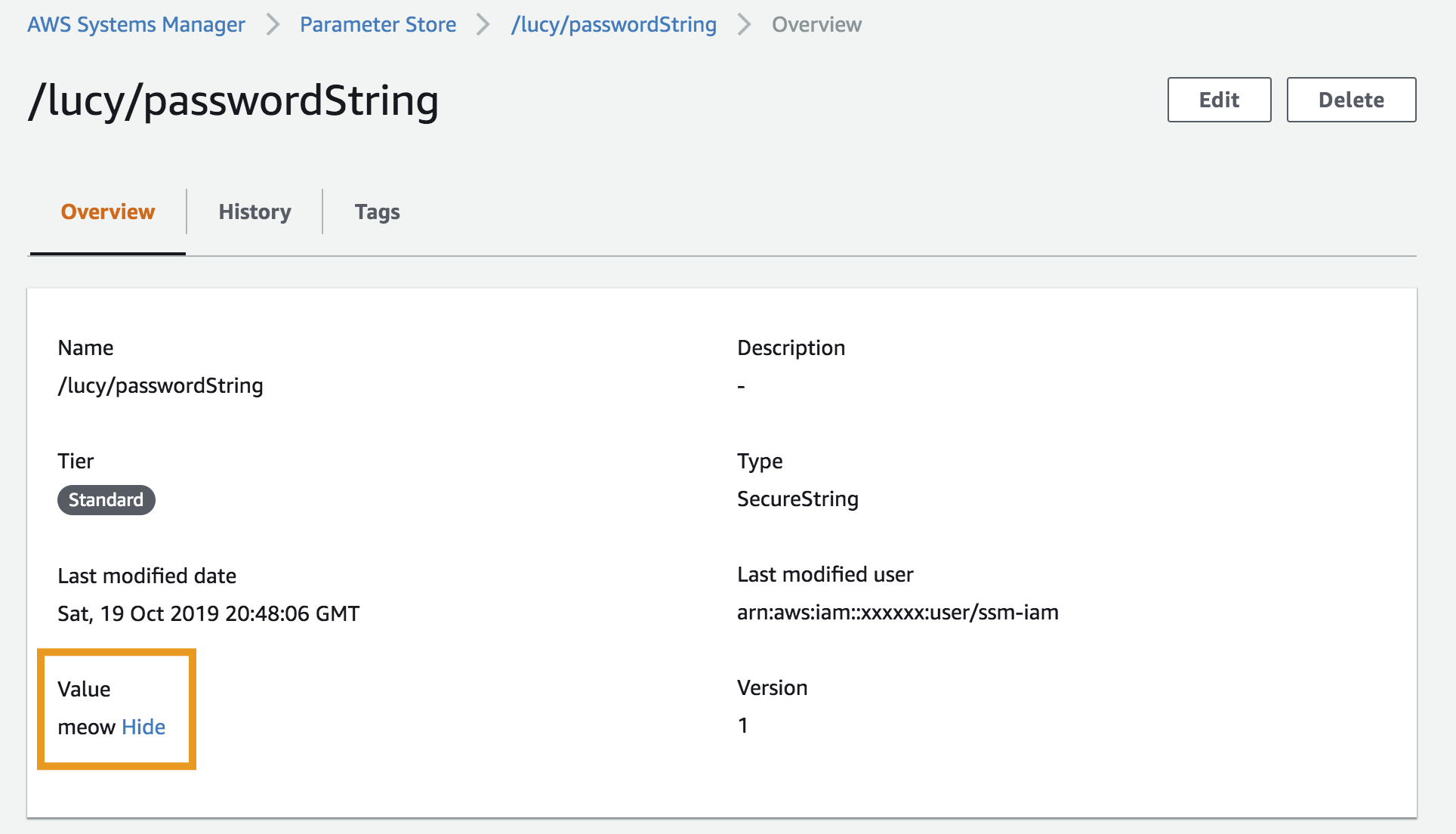



Keep Your Secrets Safe With Aws Systems Manager Parameter Store And Node Code By Amir Amir Boroumand




Agent Doing Unauthenticated Access To S3 Bucket When Enabling Output Storage To S3 Issue 299 Aws Amazon Ssm Agent Github




Blog Oblivion Cloud Control



Getting Started With Marklogic Server On Aws Marklogic Server On Amazon Web Services Aws Guide Marklogic 10 Product Documentation




The Right Way To Store Secrets Using Parameter Store Aws Management Governance Blog
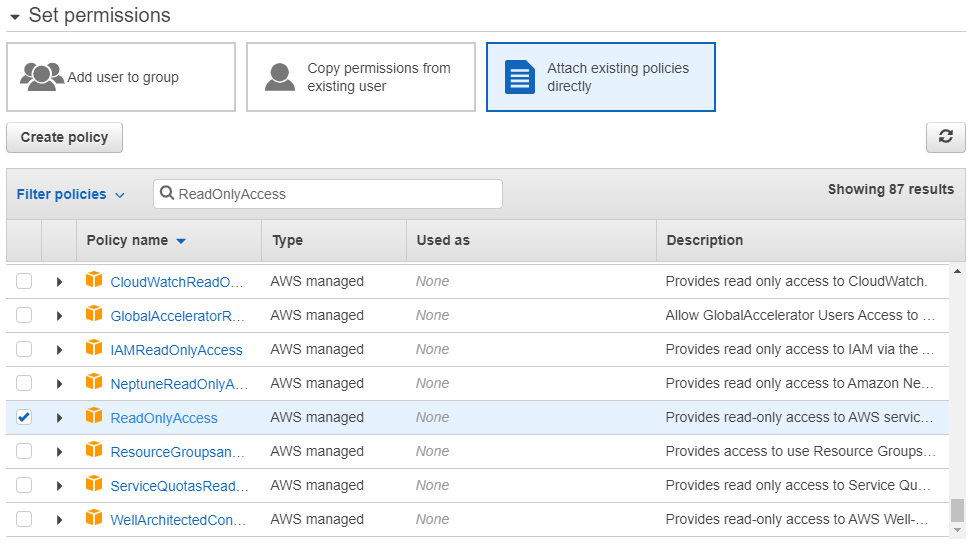



How To Grant Read Only Access On Amazon Web Services Aws By Guillermo Musumeci Medium




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog



Github Formkiq Formkiq Core Formkiq Core Is An Open Source Headless Document Management System Dms That Runs In Your Amazon Web Services Aws Cloud



Documentation Commvault Com Commvault V11 Others Pdf Commvault Amazon Sts Assumerole Activation Guide Pdf




Getting Started With Windows Workloads On Amazon Ec2



C2r0ow Yuyotm




Instance Scheduler Implementations Aws Solutions




Discovering Amazon Web Services Documentation For Bmc Discovery Content Reference Bmc Documentation




Aws Identity And Access Management Iam Noise




Amazon Web Services Aws Geekdudes
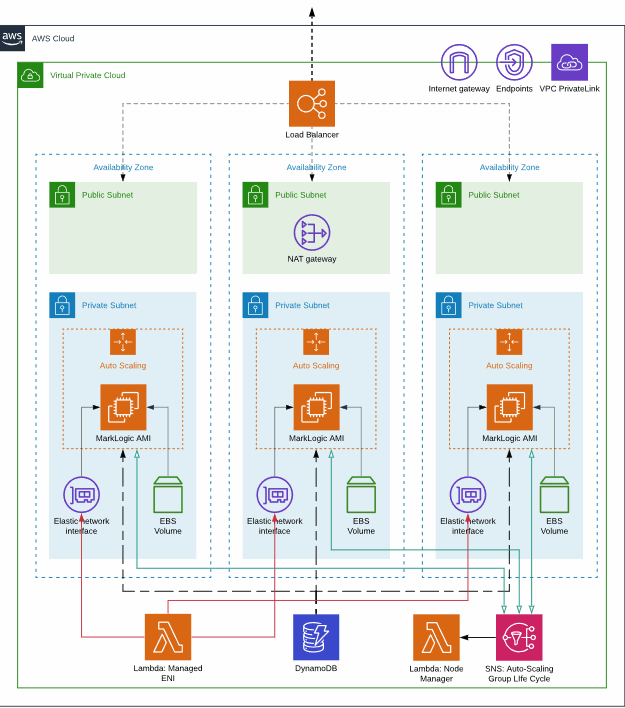



Deploying Marklogic On Ec2 Using Cloudformation Marklogic Server On Amazon Web Services Aws Guide Marklogic 10 Product Documentation
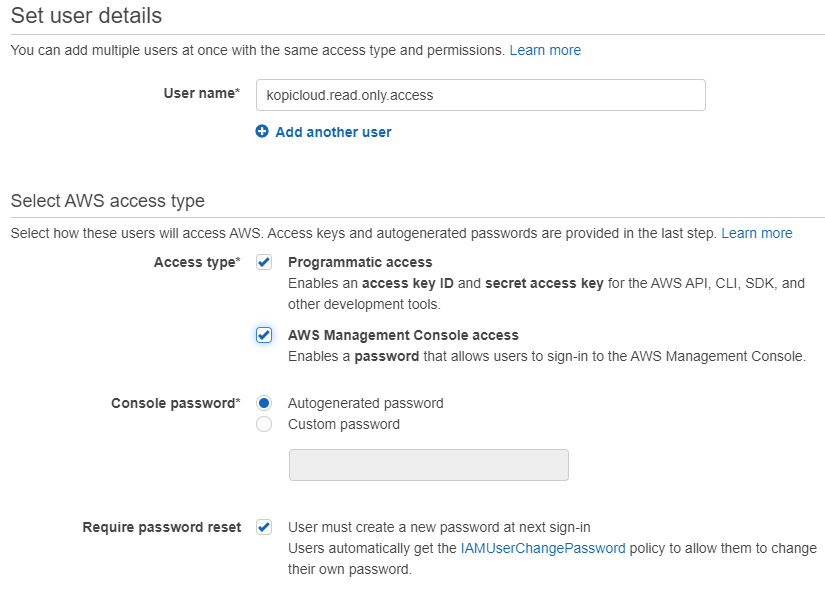



How To Grant Read Only Access On Amazon Web Services Aws By Guillermo Musumeci Medium




Replacing A Bastion Host With Amazon Ec2 Systems Manager Aws Management Governance Blog




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog



Aws Identity And Access Management Iam Roles Sts Assume Role Via Aws Cli2 21




How To Get Read Only Visibility Into The Aws Control Tower Console Aws Security Blog
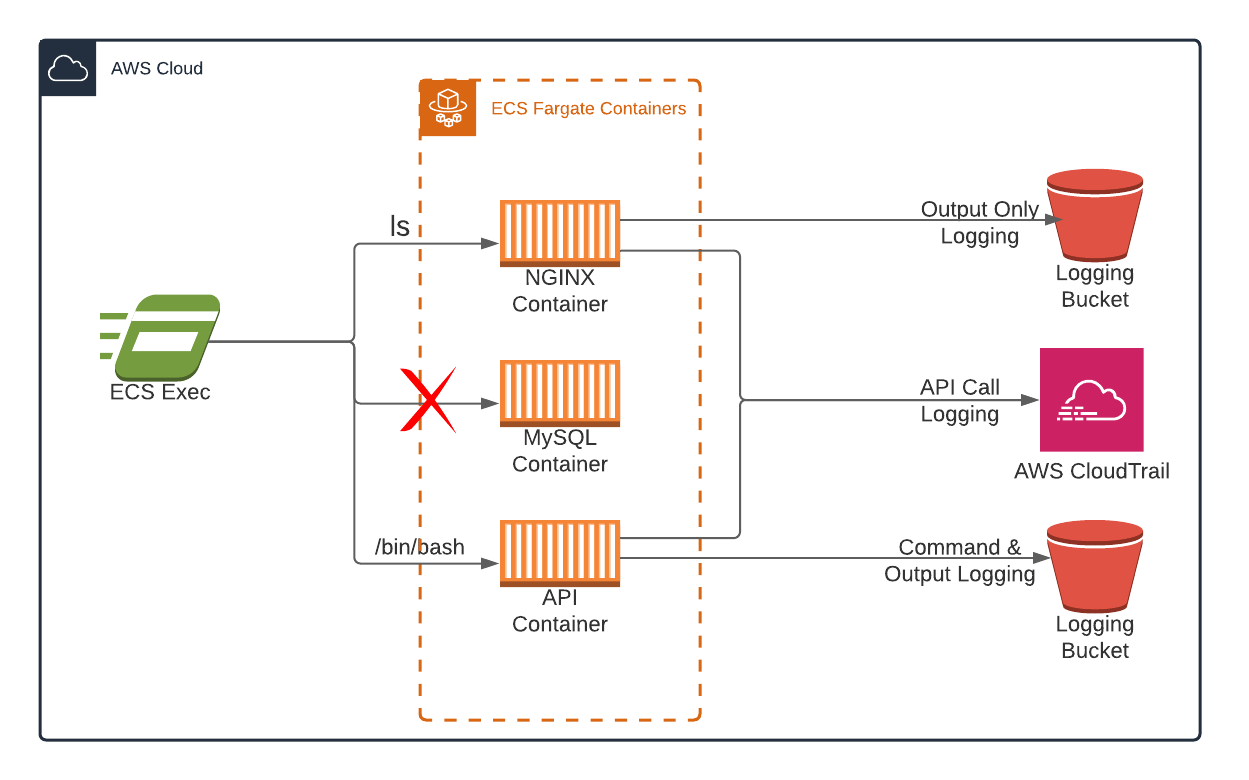



Aws Ecs Exec Feature With Fargate Terraform Implementation And Testing By Marcin Cuber May 21 Aws In Plain English



Documentation Commvault Com Commvault V11 Others Pdf Commvault Amazon Sts Assumerole Activation Guide Pdf




Aws Identity And Access Management Iam Noise



0 件のコメント:
コメントを投稿